Dirty Stick: My Encounter with PlugX Malware
I came across a real-world cybersecurity case involving a client’s system being infected with a variation of the PlugX Malware. This malware goes by many aliases, one being Korplug. This malware gives hackers unauthorized remote control over compromised systems. This is my story of how I discovered it, examined its processes, and came across its Chinese origins. I will try to provide IOCs and some tips—let’s dive into it.
Discovery: Getting the Alert (EDR)
As I was churning through some high-level tickets, I noticed an interesting one dealing with a foreign USB stick being kor-plugged into the client’s machine. Unlike regular sticks, this was imbued with malware. It mapped to the E Drive with the binary name as “Removable Disk(7GB).exe”. As you know, the naming convention is irrelevant. Files (good and bad) can undergo many names, but their contents are what matter. So I imported its SHA256 hash into VirusTotal.
- SHA256:
d813af67dd802a33109de79a613dc1fd177a7ef86137eb931aa3173d3aae5f96
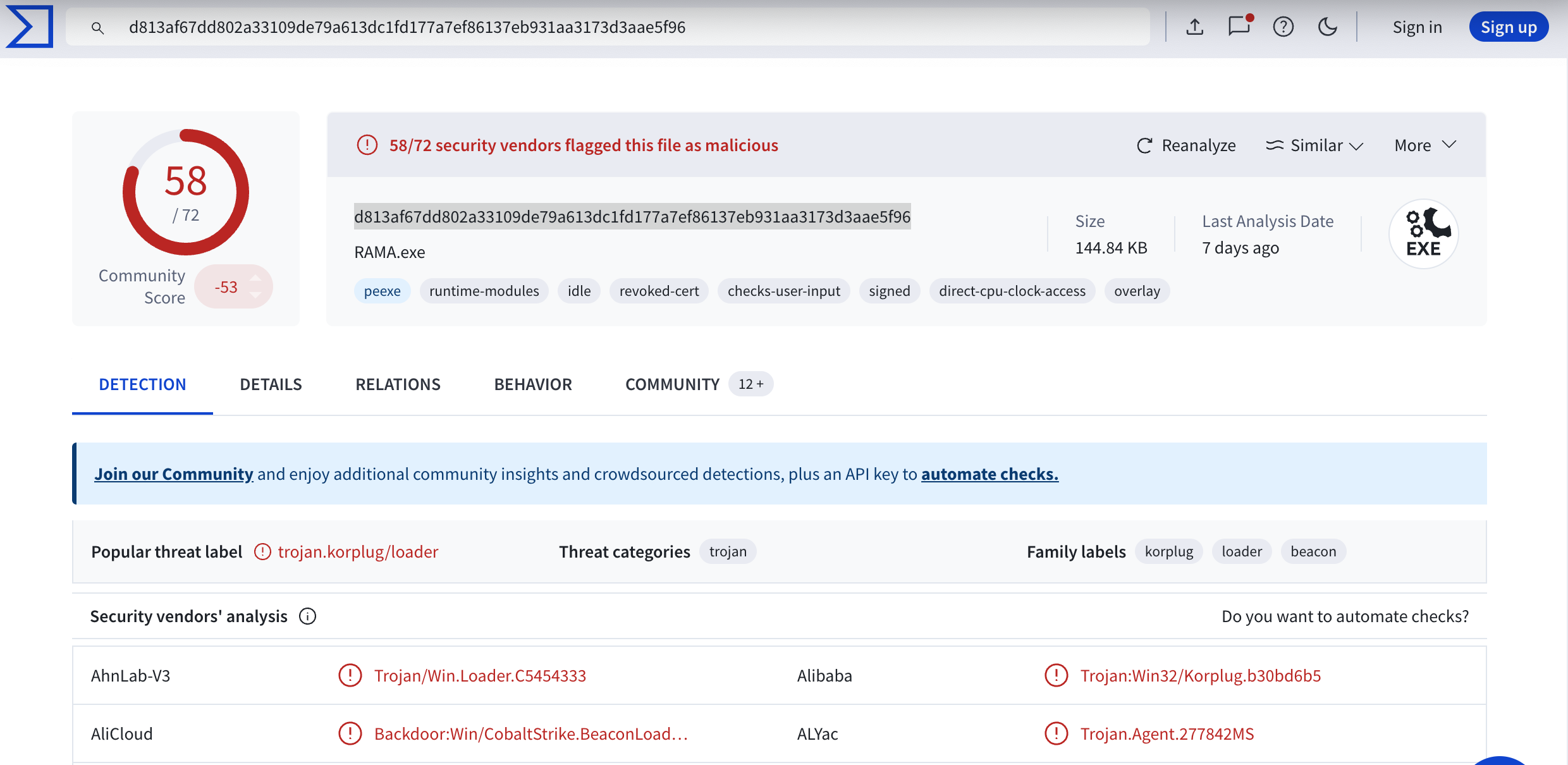
As you can see, it’s highly malicious. But I would like to talk about the processes I observed on the machine, which can offer some insights to current practitioners. We will then close with its origins.
Processes: Strange Activity
I’m a stickler for high-quality work. Instead of writing it off as another malware incident, blocking its hash, and moving along, I looked further into its processes on the infected system. Using the skills I learned in 13Cubed’s Investigating Windows Memory course (which you can find my review here), I summarized the following tree below:
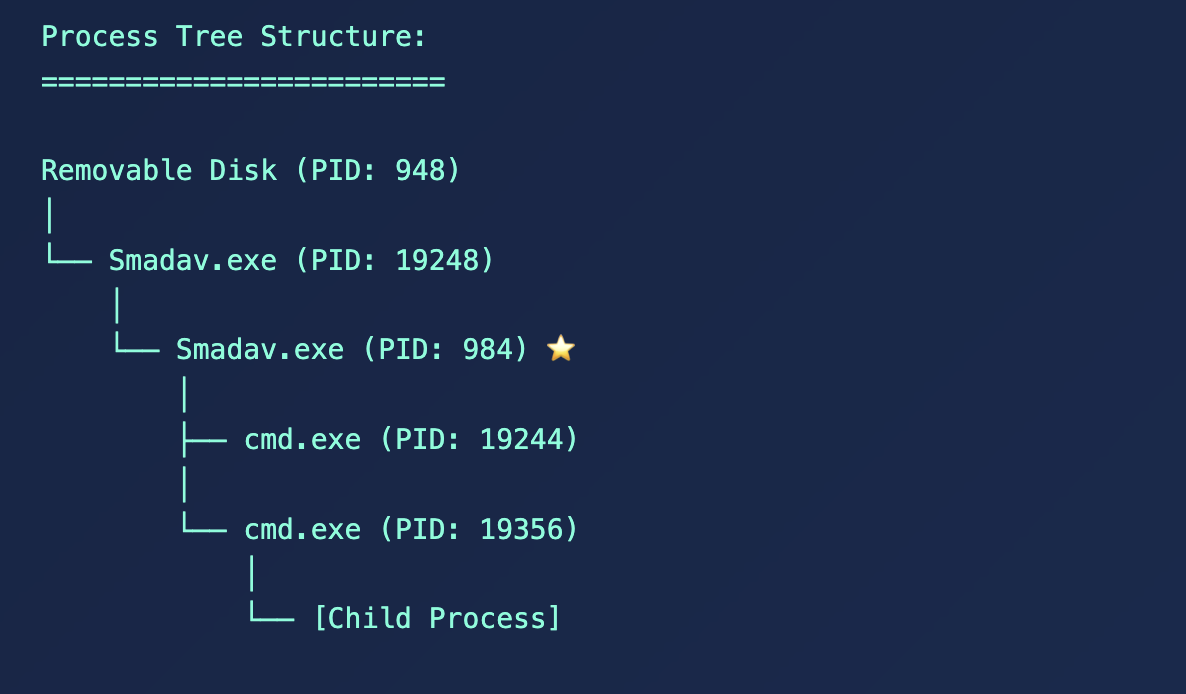
Now, the parent process for PID 948 was explorer.exe—a Windows system process for the graphical shell. This is launched automatically when a user logs into their Windows account. This tells me the following: the user successfully unlocked the Windows workstation, then inserted the USB stick, which contained the malicious program that launched immediately. Was this an inside job? We cover that theory later.
The PID 948 then launches PID 19248 in the following path: E:\RECYCLERS.BIN\Smadav.exe. The Recyclers bin is NOT a standard Windows directory where legitimate software should run from. When you examine VirusTotal, this is expected for this malware:
C:\Users\<USER>\AppData\Local\Temp\RECYCLERS.BIN\Smadav.exe
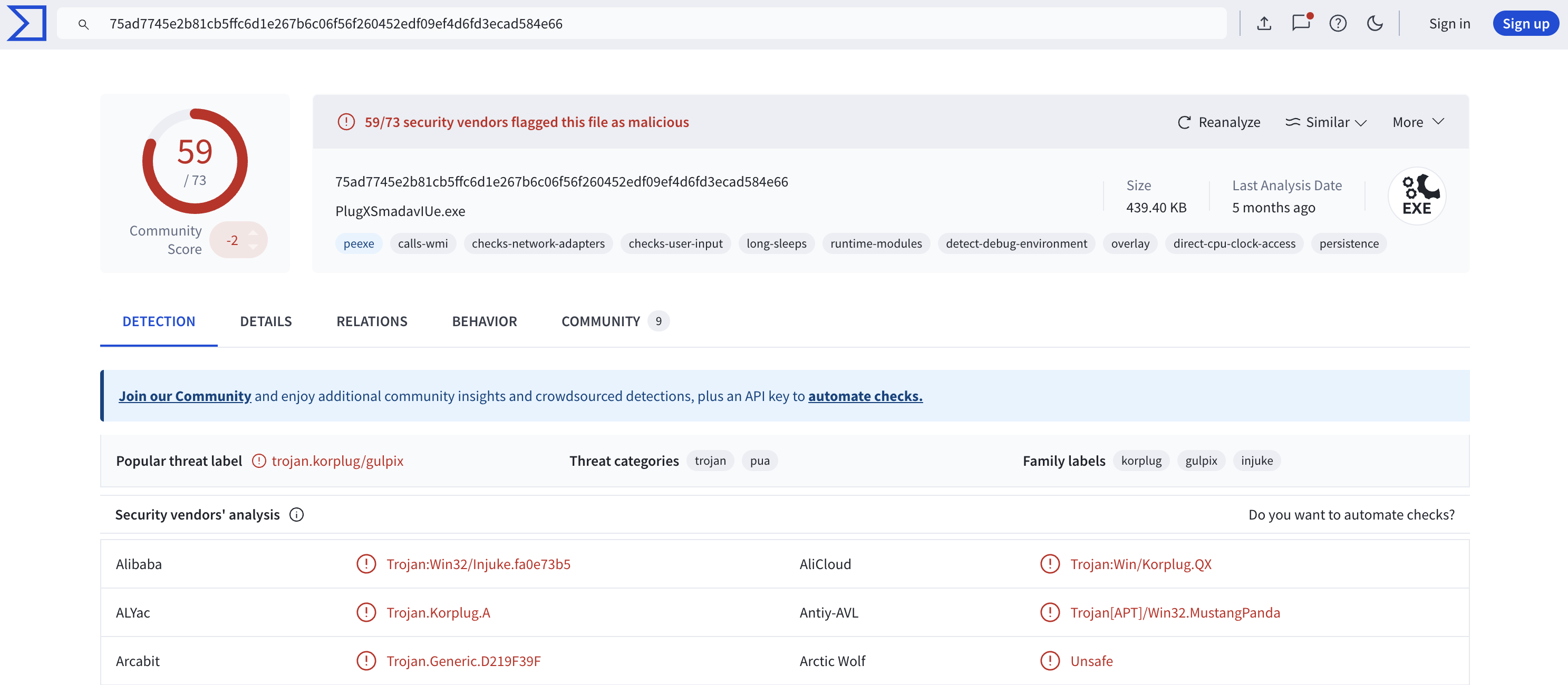
What is puzzling is that the program Smadav.exe, according to its website, is a free-to-download program that serves as a second-layer antivirus protection for your device and USB flash drive. The second-layer antivirus spawned from the malicious binary. This is most likely the malware masquerading as security software—the irony. It was further confirmed by its hash:
- SHA256:
75AD7745E2B81CB5FFC6D1E267B6C06F56F260452EDF09EF4D6FD3ECAD584E66
This binary is highly malicious per VirusTotal. It is labeled as PlugX—rightfully so. Remember what I said earlier: the naming convention is irrelevant, hence why I was puzzled at the antivirus name earlier. Its contents will show what it is.
PID 19248 then drops another executable PID 984, this time on the host:
C:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
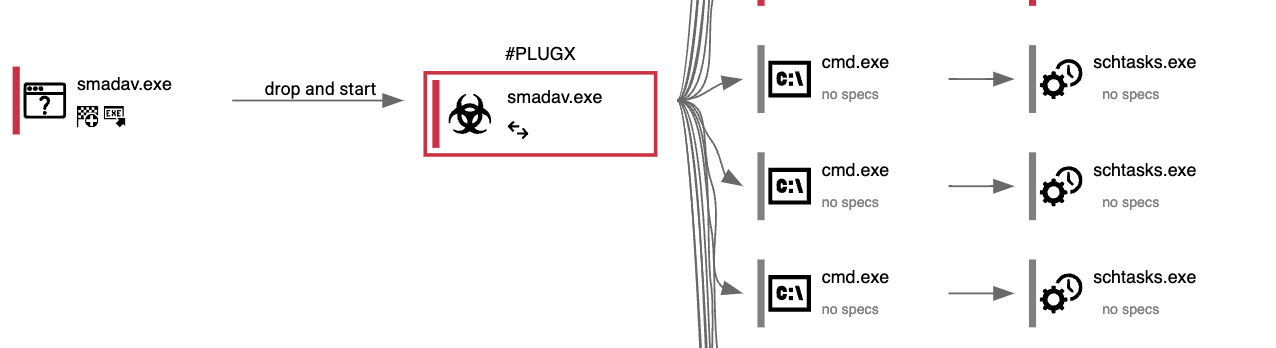
Afterwards, I noticed a plethora of cmd.exe commands running. The arguments were created scheduled tasks, manipulating Windows registry entries, and other things. This article by Twingate covers a bit more of its actions; I would like to focus on the scheduled tasks I visibly saw on the machine:
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /delete /tn "udisk_1" /f
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /create /sc minute /mo 10 /tn "Autodesk plugin" /tr """C:\ProgramDa...
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /run /tn "Autodesk plugin"
C:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /run /tn "Autodesk plugin"
C:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /create /sc minute /mo 10 /tn "Autodesk plugin" /tr """C:\ProgramDa...
C:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
"C:\Windows\System32\cmd.exe" /c SCHTASKS.exe /delete /tn "Autodesk plugin" /f
C:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
In this, we see it using the “Autodesk plugin” as the task name to appear legit; it also created a task to run every 10 minutes, and stored itself in the C:\ProgramData path.
PlugX can establish communication with command and control (C2) servers using HTTP and HTTPS ports. This allows the threat actor to control the system remotely to send further commands. I noticed in the process actions that it made an outgoing, successful connection to two IPs via the source port 63183. Please note: these connections were made AFTER a multitude of commands were run:
96.7.169[.]183(Dest Port: 443) (VT Results)43.254.217[.]165(Dest Port: 8000) (VT Results)
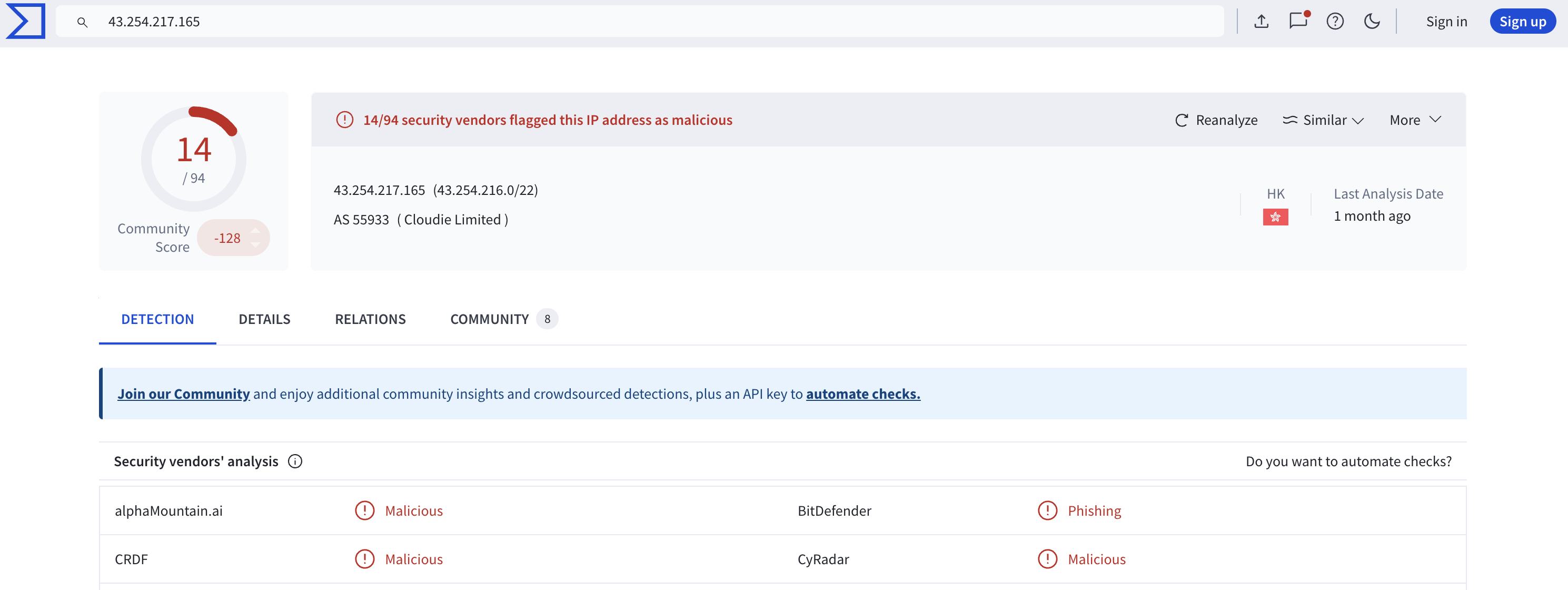
As you can see, the second IP is malicious, which points to Hong Kong, China. Now, let’s talk about its origin group: Mustang Panda.
Mustang Panda
I mentioned this malware has Chinese origins, and the IOCs were a testament to it. The group Mustang Panda has recently been increasing its espionage campaigns across Europe, mainly targeting maritime transportation companies and governmental institutions. According to Cyber Security News, “The group has been leveraging Korplug loaders and malicious USB drives as primary attack vectors.” As someone currently within the maritime transportation field, this is something I experienced firsthand. As the article explains, the execution chain begins when a user inserts an infected drive, which triggers an autorun feature. I am unsure how the dirty stick came in contact with the user, which bothers me. Nevertheless, the threat to that host is currently eliminated. I am sure I will come across them again.
Conclusion
This blog is my personal experience with Mustang Panda Korplug malware. I suggest you read the following findings to learn more about this APT:
- Google Cloud: Infected USB drives used to steal secrets
- Cyber Security News: Chinese APT Hackers Attacking Organizations via Korplug Loaders
IOCs Summary
File Hashes:
- Initial USB executable:
d813af67dd802a33109de79a613dc1fd177a7ef86137eb931aa3173d3aae5f96 - Smadav.exe (PlugX):
75AD7745E2B81CB5FFC6D1E267B6C06F56F260452EDF09EF4D6FD3ECAD584E66
IP Addresses:
96.7.169[.]183:44343.254.217[.]165:8000
File Paths:
E:\RECYCLERS.BIN\Smadav.exeC:\ProgramData\Smadav\SmadavNSK\Smadavexe.807
Scheduled Task:
- Task Name: “Autodesk plugin”
- Frequency: Every 10 minutes